Gsm Key Generation And Encryption
- Free Key Generation Software
- Key Generation Software
- Gsm Key Generation And Encryption Windows 10
- Gsm Key Generation And Encryption Key
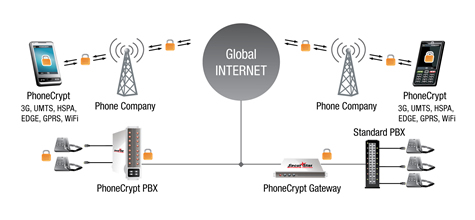
The GSM authentication, session key generation, and encryption processes are depicted in Figure 2. GSM Authentication, Session key generation, and Ciphering The anonymity in the GSM is provided by replacing the use of IMSI with a 32-bit Temporarily Mobile Subscriber Identity (TMSI). TMSI is typically handled. It uses 10-bits key size for encryption. It is a symmetric cipher. It has Two Rounds. Let’s start the game! Key Generation of S-DES or How to Generate the Key of Simplified DES. First and foremost, we need to generate a key. With the help of this key we will encrypt the message.
Free Key Generation Software
Meet escalating security and performance requirements with the new algorithms and protocols for encryption, authentication, digital signatures, and key exchange in Cisco Next-Generation Encryption (NGE).
Many of the algorithms that are currently in extensive use cannot effectively scale to meet today's changing security and performance needs. For example:
- RSA signatures and Diffie-Helman (DH) key exchange are increasingly inefficient as security levels rise.
- Cipher Block Chaining (CBC) encryption performs poorly at high data rates.
- IPsec VPNs use numerous component algorithms, limiting security to the lowest security level of each component.
What you need is the complete algorithm suite in Cisco NGE. In this suite, each component provides a consistently high level of security, and can effectively scale to high throughput and large numbers of connections.
Key Generation Software
Advances in Cryptography
Cisco NGE technology offers a complete algorithm by using:
- Elliptic curve cryptography (ECC) to replace RSA and DH
- Galois/Counter Mode (GCM) of the Advanced Encryption Standard (AES) block cipher for high-speed authenticated encryption
- SHA-2 for Hashing operations to replace MD5 and SHA-1
Gsm Key Generation And Encryption Windows 10
The algorithms that make up NGE are the result of more than 30 years of global advances and evolution in cryptography. Each component of NGE has its own history, depicting the diverse history of the NGE algorithms, and their longstanding academic and community review. NGE comprises globally created, globally reviewed, and publicly available algorithms.
Gsm Key Generation And Encryption Key
In addition, NGE algorithms are integrated into IETF, IEEE, and other international standards. As a result, NGE algorithms have been applied to the most recent and highly secure protocols for protecting user data, such as Internet Key Exchange Version 2 (IKEv2)Transport Layer Security (TLS) Version 1.2.